3 Easy Facts About Vclub Described
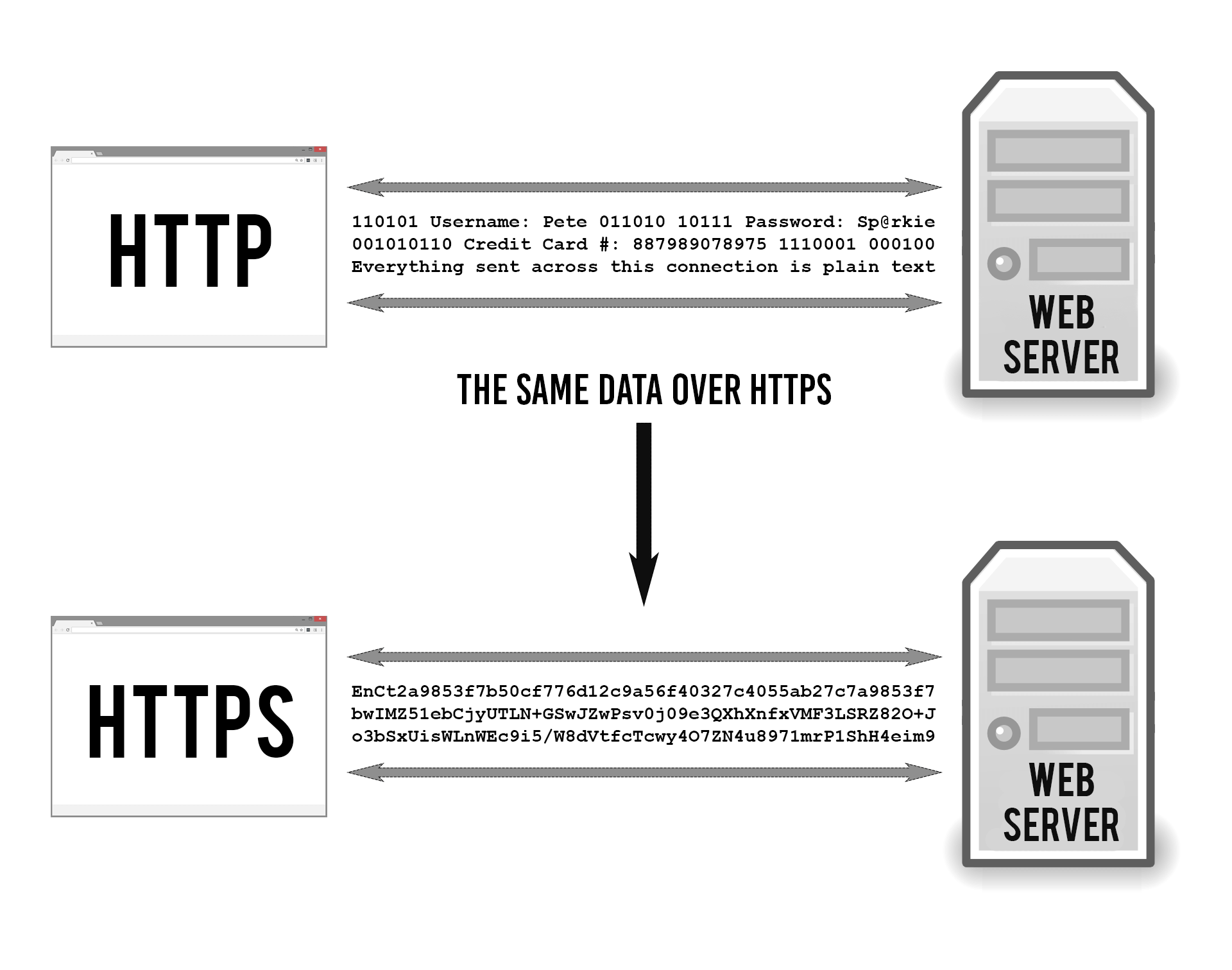
Tor is an effective file encryption browser that conceals your activities from ISPs. When you're attached to the Tor web browser, your ISP will just see that you're linked to a Tor network, yet they will not have the ability to guess your location, similar to VPNs. It needs to be kept in mind here that the Tor internet browser isn't entirely devoid of dangers.
Note: The sender and receiver are free to use either essential for file encryption or decryption, however when a secret
4 Easy Facts About Vclub Shown
has been used for encryption, file encryption can not be used for decryption and vice versa - vclub. Currently that we've covered the two kinds of security, we'll lay out 5 go to this website encryption standards that are made use of for protecting data
. With that claimed, also though the Triple DES security click for more info formula is very effective, its regime as an excellent file encryption algorithm might be coming to an end because of the tiny block size it makes use of.
If your data is secured, though, hackers will certainly look in other places for targets who have not made use of file encryption for security. Allow's not fail to remember that ISPs can get in touch with copyright giants to allow them understand if you used their network to download something unlawfully.